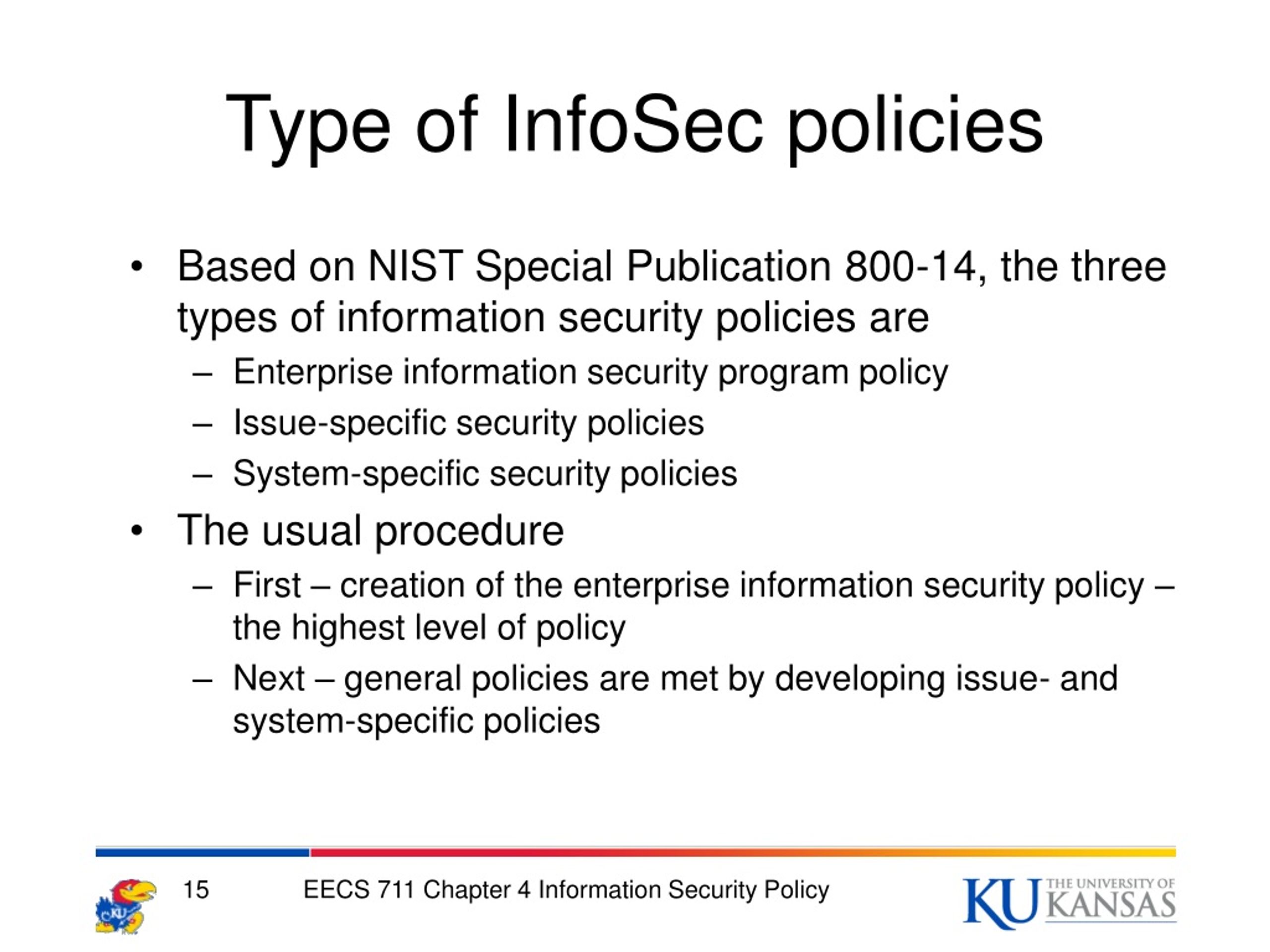
System-specific Security Policy
System-specific security policy. Thereof what is a system security policy. NIST SP 800-137 under System-Specific Security Control from CNSSI 4009. It is meant to present the approved software hardware and hardening methods for that specific system.
Addresses specific areas of technology like Electronic mail Use of the Internet. The body of rules and practices used to protect a particular information system. It is the strategic plan for implementing security in the organization.
The ISSP is designed to regulate the use of. Issue-Specific Security Policy ISSP As various technologies and processes are implemented certain guidelines are needed to use them properly The ISSP. Use of company-owned networks and the Internet Use of telecommunications technologies fax and phone Use of electronic mail Specific minimum configurations of.
Those are some explanations about security policy examples their uses and functions as well as several types. Access Control physical and digital Compliance. A System-Specific Security Policy is different from a typical Enterprise Information Security Policy or Issue-Specific Security Policy in that it governs how one particular system is set up and maintained.
A system-specific policy is. A system-specific policy is a policy written for a specific system or device and may change with changes in the system or device its functionality or its vulnerabilities. This short video examines the topic of system specific security policy and its components.
A System-Specific Security Policy is different from a typical Enterprise Information Security Policy or Issue-Specific Security Policy in that it governs how one particular system is set up and. Security policy is a definition of what it means to be secure for a system organization or other entity. The issue-specific security policy is a security policy that provides detailed targeted guidance to instruct employees in the proper use of a resource such as an information asset or technology.
So we have to write security policy under system and information types. Issue-Specific Security Policy ISSP Addresses specific areas of technology Requires frequent updates Contains a statement on the organizations position on a specific issue May cover.
Issue-Specific Security Policy is one among three other Information security Policy.
A system-specific policy is. The ISSP is designed to regulate the use of. Continue to order Get. System Specific Policy SSP It is a policy that is given specifically for the system because in a company there may be some policies that are not appropriate and therefore it is necessary to develop policies that are specific to each system. Issue-specific policies may cover electronic mail use of internet Home use of company-owned computer equipment use of personal equipment on company networks use. Those are some explanations about security policy examples their uses and functions as well as several types. Security policy is a definition of what it means to be secure for a system organization or other entity. System-specific policy is limited to the system or systems affected and may change with changes in the system its functionality or its vulnerabilities. Answer 1 of 2.
I found Issue-specific security policies ISSP more common policy used by business and organizations. System Specific Policy SSP It is a policy that is given specifically for the system because in a company there may be some policies that are not appropriate and therefore it is necessary to develop policies that are specific to each system. So we have to write security policy under system and information types. Answer 1 of 2. Use of company-owned networks and the Internet Use of telecommunications technologies fax and phone Use of electronic mail Specific minimum configurations of. A System-specific policy is concerned with a specific or individual computer system. Issue-Specific Security Policy ISSP Addresses specific areas of technology Requires frequent updates Contains a statement on the organizations position on a specific issue May cover.








































Post a Comment for "System-specific Security Policy"